ISO/IEC TS 27022:2021 – Information technology – Guidance on information security management system processes
Richard Green, CQP FCQI, Managing Director of Kingsford Consultancy Services, UK, outlines the newest guidance on information security implementation and operation.
In the early days of management systems, a high degree of emphasis was placed on operating in accordance with specific, designated procedures. Management system standards were highly prescriptive, not only telling organisations which procedures they needed to create, but also specifying the content to a large extent. This approach severely limited the ability of organisations to introduce creative solutions.
Following a major revision of ISO 9001 in 2000, there was a switch from procedures to processes and the advent of the process approach. The process approach tell us that the best results are obtained when all business processes operate as an integrated and complete system, as opposed to being operated in isolation from each other. By using plan, do, check, act to continually improve the way processes are delivered and risk-based thinking to ensure a focus on those processes most critical to service delivery, organisational performance is maximised.
ISO/IEC TS 27022:2021
Despite the process approach being more than 20 years old, it still remains something of a dark art. Although the principles behind it are well understood, it is often poorly implemented. Recognising this, ISO/IEC 27022:2021 was created by Information Technology Sub Committee 27 – Information security, cybersecurity and privacy protection. ISO/IEC 27022:2021 is designed to assist with the incorporation of the process approach into an information security management system (ISMS).
As well as presenting an ISMS process reference model (PRM), this new technical standard is designed to complement the requirements-orientated perspective within existing ISO/IEC 27000 series standards by providing an operational, process-orientated point of view.
Process reference model
ISO/IEC TS 27022 defines three types of processes: management, core and support.
Clause 6 concentrates on management processes. These are processes “that define the objectives of the management system” and include IS governance and management interface processes.
Clause 7 focuses on core processes. These represent the major elements of the ISMS and are processes which “deliver apparent and direct customer value”. ISMS core processes include (but are not limited to) security policy management processes, information security (IS) risk assessment processes, IS risk treatment processes, processes to control outsourced services and IS improvement processes.
Clause 8 deals with support processes “support core processes by providing and managing necessary resources without delivering direct customer value”. Examples include record control processes, resource management processes, communication processes and IS customer relation processes.
Each ISMS process is then described in terms of:
- process category
- a brief description
- objectives/purposes
- its inputs
- its results
- activities/functions
- references (to other ISMS standards/clauses).
These process descriptions are referred to as the fundamental elements of the PRM and each is captured within a common template. A modified example is shown below.
|
Process name |
Security policy management process |
|
Process category |
Core process |
|
Brief description |
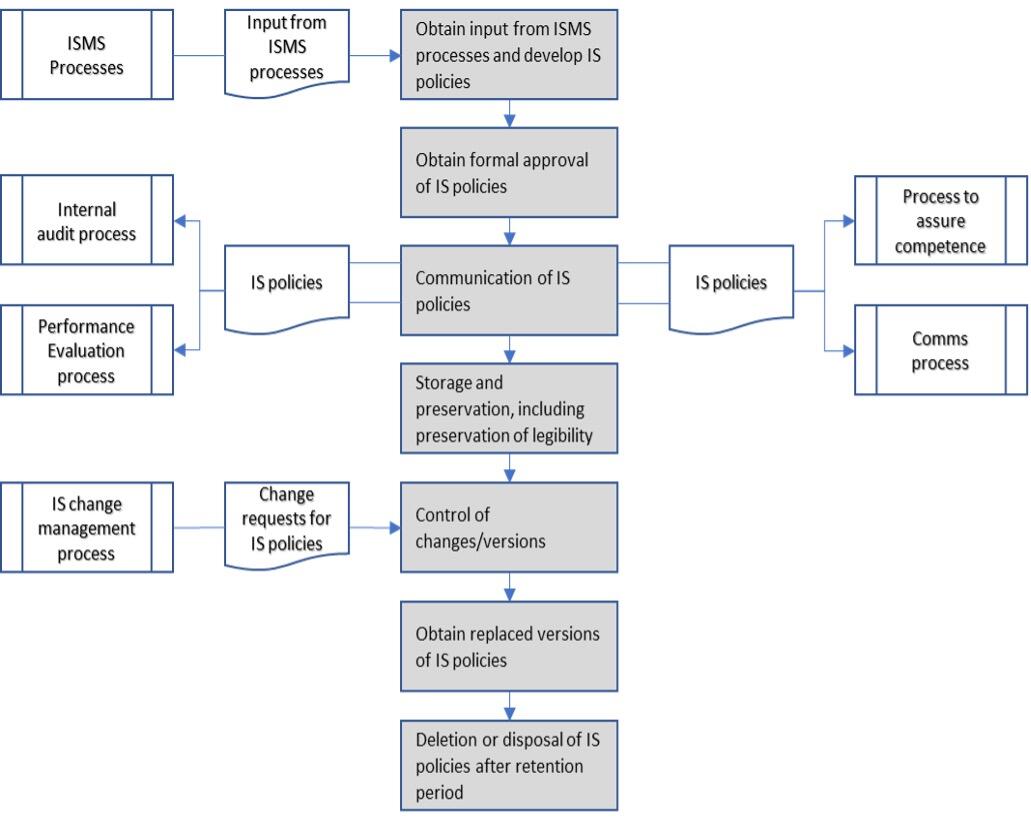
The security policy management process is the process to develop, maintain and retain IS policies, standards, procedures and guidelines (referred to as IS policies). |
|
Objectives/purpose |
To ensure that appropriate policies, standards, procedures and guidelines regarding IS are developed, maintained, available and understood by relevant stakeholders. |
|
Input |
From all other IS processes, results of processes. From change management process, necessary changes of policies in the form of change requests. |
|
Results |
For communication processes, internal audit process, performance evaluation process, record control process, processes to ensure awareness and competence. |
|
Activities/functions |
Obtain input from ISMS processes and develop IS policies; Obtain formal approval of IS policies; Communication of IS policies; Storage and preservation, including preservation of legibility; Control of changes/versions; Obtain replaced versions of IS policies; Deletion or disposal of IS policies after retention period. |
|
References |
ISO/IEC 27001:2013 5.2, 7.4, 7.5; ISO/IEC 27003:2017 5.2, 7.4, 7.5, and Annex A. |
Applicability
The PRM in ISO/IEC TS 27022 is applicable to all organisations operating ISO/IEC 27001 ISMS.
This new technical standard will provide a definite benefit for those who are unsure how the processes specified in ISO/IEC 27001 should be constructed and how they should work together. Even organisations that have been using ISO 27001 for some time will find this a useful document against which to check their existing systems.